AI Deepfake vs Facial Biometric: The Battle for Secure Authentication
Table of Contents
In recent years, Artificial Intelligence (AI) has grown rapidly, bringing many changes to our everyday lives and the technology we use. AI helps computers perform tasks that usually require human intelligence, like recognizing speech, identifying images, and making decisions. This growth has been fueled by the increasing demand for AI development services, which provide the expertise and tools necessary to create advanced AI solutions.
One of the fascinating but potentially dangerous developments in AI is deepfake. Deepfakes use AI to create realistic but fake videos or images of people. These can be so convincing that it is hard to tell they are not real. On the other hand, facial biometrics is a technology that uses AI to recognize and verify people’s identities based on their facial features. This technology is widely used for security purposes, like unlocking smartphones, accessing secure areas, and verifying identities online.
As we rely more on digital technology, secure authentication – the process of verifying that someone is who they claim to be – becomes increasingly important. Both deepfakes and facial biometrics play significant roles in this area, but they are at odds with each other. While facial biometrics aims to improve security, deepfakes can undermine it by creating false identities.
This blog will explore the ongoing battle between AI deepfakes and facial biometrics in the context of secure authentication. We will examine how deepfakes pose a threat to security systems and how facial biometrics is evolving to counter these threats, ensuring that our digital interactions remain safe and trustworthy.
Understanding AI Deepfakes
Deepfakes are realistic but fake videos or images created using AI technology. The term “deepfake” comes from “deep learning“, a type of AI, and “fake”. Deepfakes first gained attention around 2017 when people started using AI to swap faces in videos, making it look like someone was doing or saying things they never did. Since then, the technology has advanced rapidly, making deepfakes more convincing and harder to detect.
Technology Behind Deepfake: GANs (Generative Adversarial Networks)
The main technology behind deepfakes is called Generative Adversarial Networks, or GANs. GANs consist of two parts: a generator and a discriminator. The generator creates fake images or videos, while the discriminator tries to tell if these creations are real or fake. The two parts compete against each other, with the generator getting better at creating realistic fakes and the discriminator improving at detecting them. This process continues until the generator produces images or videos that are so realistic they can fool most people and sometimes even the discriminator.
Examples of Deepfakes in Media and Their Impact
Deepfakes have been used in various ways, some harmless and others harmful. For example, deepfakes have been used in entertainment to bring actors back to life in movies or to create funny videos swapping celebrities’ faces. However, deepfakes have also been used maliciously, such as creating fake news videos to mislead people, spreading misinformation, or creating non-consensual explicit content. These harmful uses can have significant negative impacts, including damaging reputations, influencing public opinion, and creating mistrust in the media.
The Threat Posed by Deepfakes in Security and Authentication
Deepfakes pose a serious threat to security and authentication systems. Since they can create highly realistic fake videos and images, deepfakes can be used to trick facial recognition systems, bypass security checks, and impersonate individuals in secure communications. This can lead to unauthorized access to sensitive information, financial fraud, and other security breaches. As deepfake technology continues to improve, it becomes increasingly challenging to distinguish between real and fake media, making it essential to develop advanced detection methods and improve security protocols to protect against these threats.
Facial Biometrics: The Basics
Facial biometrics is a technology that identifies and verifies people based on their facial features. This technology has been around in various forms for decades, but it has become much more advanced and accurate with the development of AI and machine learning. Initially used in specialized security settings, facial biometrics are now widely used in everyday devices and applications, such as smartphones and social media.
How Facial Recognition Technology Works: Key Algorithms and Processes
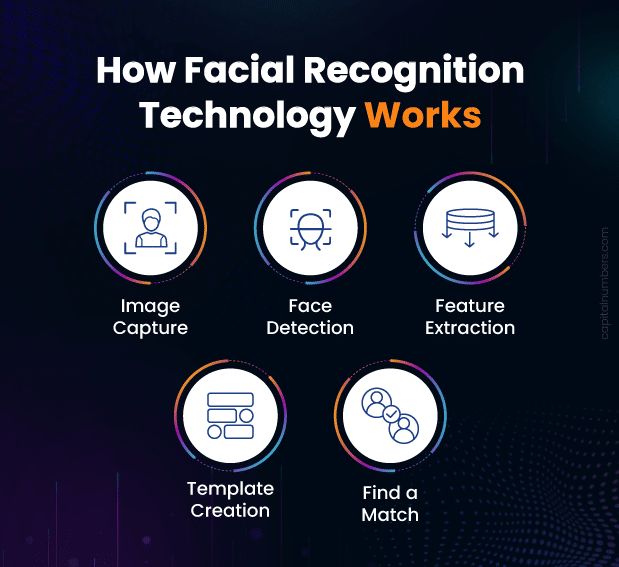
Facial recognition technology involves several key steps:
- Image Capture: A camera captures an image or video of a person’s face.
- Face Detection: The system detects the face in the image, identifying its position and size.
- Feature Extraction: The system analyzes the face and extracts unique features, such as the distance between the eyes, the shape of the nose, and the contour of the lips. This step often uses algorithms like Principal Component Analysis (PCA) and Linear Discriminant Analysis (LDA).
- Template Creation: These unique features are converted into a digital template or a numerical representation of the face.
- Matching: The system compares this template to a database of stored facial templates to find a match. Techniques like neural networks and deep learning models, such as Convolutional Neural Networks (CNNs), are commonly used in this step.
Applications of Facial Biometrics in Security and Authentication
Facial biometrics are used in a variety of applications to enhance security and authentication:
- Smartphones and Devices: Unlocking phones and tablets.
- Access Control: Granting access to secure buildings and rooms.
- Airports and Border Control: Verifying the identity of travelers.
- Banking and Financial Services: Confirming identity for online transactions.
- Law Enforcement: Identifying suspects and missing persons.
Benefits of Using Facial Biometrics for Secure Authentication
Facial biometrics offer several advantages for secure authentication:
- Convenience: Users can quickly and easily authenticate their identity without needing to remember passwords or carry physical keys.
- Speed: Facial recognition can rapidly verify identities, making processes like logging into devices or passing through security checkpoints faster.
- Accuracy: Advanced algorithms and AI make facial biometrics highly accurate, reducing the chances of false matches.
- Security: Since facial features are unique and hard to replicate, it provides a robust layer of security compared to traditional methods like passwords or PINs.
- Non-Intrusive: Unlike fingerprint or iris scanning, facial recognition does not require physical contact, making it more user-friendly and hygienic.
By leveraging these benefits, facial biometrics enhance security and user experience in various applications, helping to protect sensitive information and ensure secure access.
Deepfakes: A Growing Threat to Authentication
Deepfakes can create realistic fake images or videos of someone’s face. Hackers can use these deepfakes to trick facial biometric systems into thinking they are someone else. For example, if a hacker creates a deepfake video of a person, they can use it to unlock that person’s smartphone, access their secure accounts, or enter restricted areas by fooling facial recognition systems.
Potential Consequences of Successful Deepfake Attacks
The consequences of deepfake attacks on biometric systems can be severe:
- Unauthorized Access: Hackers can gain access to secure devices, buildings, or accounts, leading to data breaches and theft of sensitive information.
- Financial Loss: Fraudulent transactions and unauthorized withdrawals can result in significant financial losses for individuals and organizations.
- Reputation Damage: Deepfake attacks can damage the reputation of businesses, especially if they involve high-profile targets or result in significant data breaches.
- Legal Issues: Companies and individuals affected by deepfake attacks may face legal repercussions, especially if the attack leads to the exposure of personal or confidential information.
The Challenge of Detecting and Mitigating Deepfake Threats
Detecting and stopping deepfake threats is a challenging task:
- Sophistication of Deepfakes: Deepfake technology is continually improving, making it harder to distinguish fake videos and images from real ones.
- Detection Tools: While there are tools designed to detect deepfakes, they are not always reliable and can sometimes produce false positives or miss sophisticated fakes.
- Continuous Evolution: As detection methods improve, so do the techniques used to create deepfakes, resulting in an ongoing arms race between attackers and defenders.
- Integration with Other Security Measures: To combat deepfake threats, it’s essential to integrate facial biometrics with other security measures, such as multi-factor authentication and continuous monitoring for suspicious activity.
By understanding these challenges, organizations can take steps to enhance their security measures and protect against the growing threat posed by deepfakes, ensuring that their authentication systems remain robust and reliable.
Enhancing Facial Biometrics for Better Security
To fight against deepfakes, facial recognition technology is being improved with advanced techniques:
- 3D Face Mapping: This method creates a three-dimensional model of the face, which is much harder to fake than a 2D image. It looks at depth and contours, making it more secure.
- Infrared Imaging: Using infrared light to scan faces helps detect real skin texture and temperature, which deepfakes cannot replicate accurately.
- AI-Based Analysis: Advanced AI algorithms analyze tiny details in faces, such as skin texture and subtle movements, to spot inconsistencies that may indicate a deepfake.
Multi-Factor Authentication: Combining Facial Biometrics with Other Methods
To enhance security, it’s effective to combine facial biometrics with other authentication methods, known as multi-factor authentication (MFA):
- Password or PIN: Alongside facial recognition, users enter a password or PIN.
- Fingerprint Scanning: Adding fingerprint verification provides an additional layer of security.
- SMS or Email Verification: Users receive a code via SMS or email that they must enter to complete the authentication process.
Combining these methods makes it much harder for attackers to gain access, even if they manage to spoof one form of identification.
Continuous Authentication: Monitoring User Behavior for Anomalies
Continuous authentication goes beyond just checking a user’s identity at login. It involves constantly monitoring the user’s behavior to ensure they are who they claim to be:
- Behavioral Biometrics: This includes analyzing patterns like typing speed, mouse movements, and how a person uses their device.
- Contextual Analysis: Looking at the context of a user’s actions, such as location and time of access, to detect unusual behavior that might indicate an intruder.
- Session Monitoring: Continuously checking for signs of suspicious activity during a user’s session, which helps to quickly identify and respond to potential security breaches.
AI-Driven Anti-Spoofing Measures: Liveness Detection and Deepfake Detection Algorithms
AI-driven anti-spoofing measures are crucial for preventing deepfake attacks:
- Liveness Detection: This technique ensures that the biometric sample is from a live person and not a photo or video. It can include checking for natural eye movements, blinking, and changes in facial expressions.
- Deepfake Detection Algorithms: Specialized AI algorithms are designed to detect the subtle signs of deepfakes. These algorithms analyze the media for inconsistencies, such as unnatural lighting, edge artifacts, and irregular facial movements that are common in deepfakes.
By implementing these advanced techniques and measures, we can significantly improve the security of facial biometric systems, making it much harder for attackers to use deepfakes to bypass authentication processes.
You May Also Read: Don’t Get Hacked: Essential Software Security Checklist for Developers
Future Directions in Secure Authentication
New technologies are constantly being developed to make biometric security more robust:
- Voice Recognition: This technology identifies individuals based on their unique vocal patterns. Combining voice recognition with facial biometrics adds an extra layer of security.
- Iris Scanning: Scanning the unique patterns in the colored part of the eye, the iris, is another highly secure biometric method.
- Behavioral Biometrics: This involves analyzing patterns in how users interact with their devices, like typing speed, swipe patterns, and even walking gait. These patterns are unique to each person and hard to fake.
The Potential Role of Blockchain in Secure Authentication
Blockchain technology can play a significant role in enhancing secure authentication:
- Decentralized Identity Management: Blockchain can store and verify identities in a decentralized manner, reducing the risk of central points of failure and data breaches.
- Immutable Records: Blockchain’s immutable ledger ensures that once data is recorded, it cannot be altered or tampered with, adding a layer of trust to authentication processes.
- Smart Contracts: These are self-executing contracts with the terms directly written into code. They can automate and secure authentication processes, ensuring that identity verification is conducted fairly and transparently.
You May Also Read: Blockchain Breakthroughs: Transforming Authentication, Authorization, and Accounting
Ongoing Research and Developments in AI and Biometrics
Researchers are continuously working on improving AI and biometric security:
- Deepfake Detection: New algorithms and techniques are being developed to detect deepfakes with higher accuracy. These include analyzing tiny facial movements and inconsistencies that are hard for deepfake technology to mimic.
- AI-Powered Adaptive Learning: AI systems are being designed to learn and adapt to new types of attacks in real-time, making biometric systems more resilient to emerging threats.
- Privacy-Preserving Biometrics: Techniques like homomorphic encryption allow biometric data to be processed without being exposed, protecting user privacy while maintaining security.
Predictions for the Future: Will Deepfakes Outpace Facial Biometrics?
Looking ahead, the battle between deepfakes and facial biometrics will likely continue:
- Advancement in Deepfakes: Deepfake technology is expected to become even more sophisticated, making it increasingly difficult to distinguish between real and fake images or videos.
- Improved Detection and Security: At the same time, advancements in detection algorithms and security measures will enhance the ability to identify and counter deepfakes.
- Integrated Security Solutions: The future of secure authentication will likely involve combining multiple biometric and non-biometric methods, such as voice recognition, behavioral biometrics, and continuous authentication, to create more secure and reliable systems.
- Regulatory and Ethical Considerations: As deepfake technology evolves, there will be greater emphasis on developing regulations and ethical guidelines to manage its use and protect against its misuse.
In summary, while deepfakes will continue to pose challenges, ongoing advancements in AI, biometrics, and related technologies will strive to keep biometric security one step ahead, ensuring robust and reliable authentication methods in the digital age. Additionally, custom software development will play a crucial role in creating tailored security solutions that address specific needs and vulnerabilities, further enhancing the effectiveness of biometric systems and safeguarding against emerging threats.