How to Secure Your PHP Applications: A Detailed Guide
Table of Contents
In today’s interconnected digital landscape, where web applications power businesses, the security of PHP applications has emerged as a paramount concern. The rapid evolution of technology brings a continuous stream of new cyber threats and vulnerabilities. As a result, safeguarding your PHP-powered web solutions has become more critical than ever before. To do so, you need to follow a meticulous, step-by-step approach.
In this comprehensive guide, we will embark on a journey through the intricacies of PHP application security. From unraveling common PHP vulnerabilities to practicing secure coding techniques, we will delve into the fundamental principles of safeguarding your applications. Whether you’re using older PHP versions or have seamlessly transitioned to the latest PHP 8.3 updates, adhering to these security practices is imperative for your web application development journey. So, what to wait for? Let’s dive in.
1 Understanding Common PHP Vulnerabilities
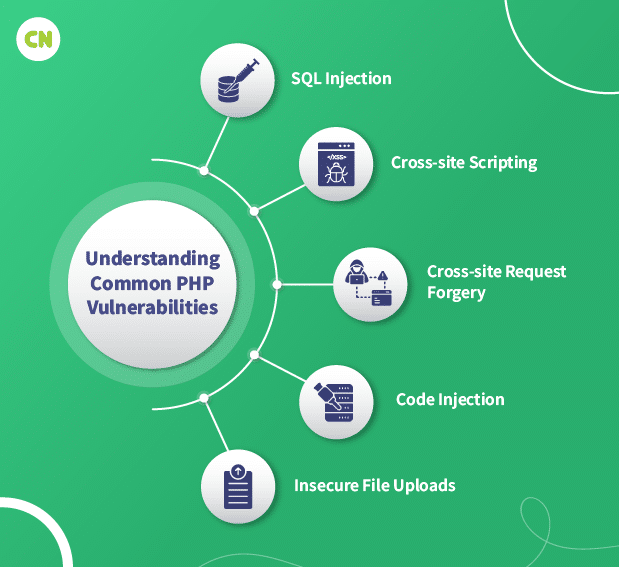
PHP applications are susceptible to various security vulnerabilities. Recognizing these PHP vulnerabilities is crucial for securing your code. Here’s an explanation of some common PHP vulnerabilities:
-
SQL Injection (SQLi)
SQL injection occurs when untrusted user input is directly concatenated into SQL queries without proper sanitization.
Example:
$user_input = $_POST['username']; $query = "SELECT * FROM users WHERE username = '$user_input'";Prevention:
Use prepared statements or parameterized queries to separate user input from SQL commands.
-
Cross-site scripting (XSS)
XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users.
Example:
echo "Welcome, " . $_GET['name'];Prevention:
Sanitize and validate user input and escape output using functions like ‘htmlspecialchars’.
-
Cross-site request forgery (CSRF)
CSRF attacks trick users into executing unwanted actions without their consent when logged in.
Example:
<img src="https://example.com/transfer?to=attacker&amount=1000" alt="Free iPhone">Prevention:
Use anti-CSRF tokens and ensure that sensitive actions require authentication.
-
Code Injection
Code injection vulnerabilities allow attackers to execute arbitrary code on the serve
Example:
$filename = $_GET['file']; include($filename);Prevention:
Avoid executing user-supplied input and validate file paths.
-
Insecure File Uploads
Attackers can upload malicious files by exploiting insecure file upload forms.
Example:
$target_dir = "uploads/"; $target_file = $target_dir . basename($_FILES["fileToUpload"]["name"]);Prevention:
Restrict file types, validate file contents, and store uploaded files outside the web root.
Understanding these vulnerabilities is the first step toward writing secure PHP code. Mitigating these risks involves implementing best practices, using certain coding techniques, and leveraging PHP security libraries and tools.
2 Secure Coding Practices in PHP
Securing PHP applications starts with adopting secure coding practices. These practices help prevent vulnerabilities and protect your application from various attacks. Here’s an overview of secure coding practices in PHP:
-
Input Validation and Sanitization
Validate and sanitize user input using ‘filter_var’ or regular expressions to ensure it adheres to expected formats. Sanitize data ‘htmlspecialchars’ to neutralize potential threats.
-
Prepared Statements and Parameterized Queries
Avoid concatenating user input in SQL queries. Instead, use prepared statements or parameterized queries with PDO or MySQLi.
-
Escaping Output Data
Escape user data before rendering it in HTML or JavaScript using ‘htmlspecialchars’ or context-specific escaping functions.
-
Avoiding Eval and Dynamic Code Execution
Refrain from using ‘eval()’ and dynamic code execution functions to prevent code injection vulnerabilities.
-
File Upload Security
Restrict allowable file types, validate uploads with ‘fileinfo’ or MIME type checks, and store files outside the web root.
-
Error Handling
Implement custom error handling, turn off display errors in production, and log errors securely.
-
Access Control and Authorization
Enforce access control and validate user permissions before granting access to resources.
-
Session Security
Generate secure session IDs, use HTTPS for data in transit, and secure session cookies.
-
Dependency Management
Keep PHP, extensions, and libraries up to date to address vulnerabilities.
-
Data Encryption
Encrypt sensitive information like passwords using ‘bcrypt’ and ‘TLS/SSL’ for data in transit.
By following these practices and incorporating them into your PHP code, you can build more secure applications and protect against common vulnerabilities.
3 Authentication and Authorization
Authentication and authorization are pivotal in web application development, serving as the gatekeepers of system security. They ensure that users are who they claim to be and control their access to resources. Here’s an explanation of both concepts:
-
Authentication
Authentication is verifying the identity of users attempting to access a system or application. It ensures that users are who they claim to be by validating their credentials, typically in usernames and passwords.
In PHP, you can implement authentication using various methods:
-
Basic Authentication: This involves sending the username and password with each HTTP request, which is then validated on the server.
if ($_SERVER['PHP_AUTH_USER'] == 'username' && $_SERVER['PHP_AUTH_PW'] == 'password') { // Authentication successful } else { // Authentication failed header('WWW-Authenticate: Basic realm="Authentication Required"'); header('HTTP/1.0 401 Unauthorized'); echo 'Authentication required.'; exit; } -
Session-based Authentication: After users log in, you can create a session to store their authentication state. Subsequent requests can then check this session to determine if a user is authenticated.
session_start(); if (isset($_SESSION['user_id'])) { // User is authenticated } else { // Redirect to login page header('Location: login.php'); exit; } -
Token-based Authentication: In modern web applications, token-based authentication is common. Users receive a unique token upon login, which they include in their requests to prove their identity.
// Generate and send a token upon successful login $token = generateToken($user_id); setcookie('token', $token, time() + 3600, '/');
-
-
Authorization
Authorization determines what actions or resources an authenticated user is allowed to access. It is enforcing access controls based on a user’s permissions and roles. In PHP, you can implement authorization using code like this:
function isAuthorized($user, $resource, $action) { // Check if the user has the necessary permissions to access the resource and perform the action // Typically, this involves querying a database or using role-based access control (RBAC). // Return true if authorized, false otherwise. } if (isAuthorized($user, 'admin_panel', 'view')) { // User is authorized to view the admin panel } else { // User is not authorized header('HTTP/1.0 403 Forbidden'); echo 'Access forbidden.'; exit; }Authorization can involve complex logic and often relies on database queries to check a user’s permissions and roles against a particular resource and action.
By implementing robust authentication and authorization mechanisms in your PHP applications, you can ensure that only authorized users access specific resources and maintain the security and integrity of your system.
4 Secure File Handling
It is crucial for web applications to prevent unauthorized access, data breaches, and code execution vulnerabilities. Here are the best practices that expert PHP developers follow to secure file handling in PHP:
-
File Uploads
When allowing file uploads from users, restrict allowed file types, validate file extensions, and use content-type checks.
Store uploaded files outside the web root directory to prevent direct access.
$uploadDir = '/path/to/uploads/'; if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadDir . $_FILES['file']['name'])) { // File uploaded successfully } else { // Handle upload failure } -
File Inclusion
Avoid using user-controlled data in functions like ‘include’ or ‘require’. Use a whitelist approach for allowed files.
$page = $_GET['page']; $allowedPages = ['home', 'about', 'contact']; if (in_array($page, $allowedPages)) { include($page . '.php'); } else { // Handle invalid page request } -
File Permissions
Set appropriate file permissions. Avoid using overly permissive settings like 777, which can expose files to unauthorized access.
chmod('/path/to/file.php', 0644); // Read and write for owner, read-only for others -
Directory Traversal
Protect against directory traversal attacks by ensuring user-supplied file paths cannot navigate outside the intended directory.
$file = '/path/to/user/supplied/file.txt'; $basePath = '/path/to/allowed/directory/'; if (strpos(realpath($file), $basePath) === 0) { // File is within the allowed directory // Proceed with operations } else { // Handle invalid file path } -
File Deletion
Be cautious when deleting files. Ensure that the file to be deleted is under your control and not based on user input.
$fileToDelete = '/path/to/file.txt'; if (file_exists($fileToDelete) && is_writable($fileToDelete)) { unlink($fileToDelete); } else { // Handle file deletion failure } -
File Content Sanitization
Sanitize user-generated file content before displaying it to prevent cross-site scripting (XSS) attacks when displaying user-uploaded content.
$fileContent = file_get_contents('/path/to/user/uploaded/file.txt'); echo htmlspecialchars($fileContent, ENT_QUOTES, 'UTF-8'); -
File Streaming
When serving files, use server-side scripts to control access and prevent direct linking to files. Stream files using PHP to apply access controls.
$file = '/path/to/protected/file.pdf'; header('Content-Type: application/pdf'); header('Content-Disposition: inline; filename="file.pdf"'); header('Content-Length: ' . filesize($file)); readfile($file);
By following these secure file-handling practices, you can protect your PHP applications from common security vulnerabilities related to file operations.
5 Database Security in PHP
Database security is vital to protect sensitive data in PHP applications. Here are key practices and code examples to enhance database security:
-
Use Prepared Statements
Utilize prepared statements and parameterized queries to prevent SQL injection attacks.
$username = $_POST['username']; $password = $_POST['password']; $stmt = $pdo->prepare('SELECT * FROM users WHERE username = :username'); $stmt->bindParam(':username', $username); $stmt->execute(); $user = $stmt->fetch(); -
Escaping User Input
When not using prepared statements, sanitize and escape user input before using it in SQL queries.
$unsafeInput = $_POST['input']; $safeInput = mysqli_real_escape_string($conn, $unsafeInput); $query = "SELECT * FROM table WHERE column = '$safeInput'"; -
Secure Database Connection
Store database credentials securely and avoid hardcoding them in source code.
$dbHost = 'localhost'; $dbName = 'mydb'; $dbUser = 'myuser'; $dbPass = 'mypassword'; $pdo = new PDO("mysql:host=$dbHost;dbname=$dbName", $dbUser, $dbPass); -
Least Privilege Principle
Assign the least privilege required to database users. Avoid using superuser accounts in your application.
GRANT SELECT, INSERT, UPDATE, DELETE ON mydb.* TO 'myuser'@'localhost'; -
Error Handling
Implement proper error handling for database connections and queries. Avoid displaying database errors to users.
try { $pdo = new PDO("mysql:host=$dbHost;dbname=$dbName", $dbUser, $dbPass); $pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION); } catch (PDOException $e) { die("Database connection failed: " . $e->getMessage()); } -
Data Validation
Validate data before inserting it into the database to ensure it meets the expected criteria.
$email = $_POST['email']; if (filter_var($email, FILTER_VALIDATE_EMAIL)) { // Valid email, proceed with database operation } else { // Handle invalid email } -
Secure Session Handling
Store session data securely and avoid exposing sensitive information in session variables.
session_start(); $_SESSION['user_id'] = $user_id; // Store minimal data -
Regular Backups
Implement regular database backups to recover data in case of security incidents.
-
Implement Access Controls
Implement role-based access controls to restrict user privileges based on their roles.
-
Security Updates
Keep your database management system (e.g., MySQL) and PHP up to date with security patches.
By implementing these best practices, you can enhance the security of your PHP application’s database interactions and protect sensitive data from potential threats.
6 Web Security
Securing PHP applications is essential to protect against various security threats. Here are key aspects of web security in PHP applications, along with relevant code examples:
-
Securing Form Data
Sanitize and validate user inputs to prevent SQL injection and other attacks.
// Validate and sanitize user input $name = filter_var($_POST['name'], FILTER_SANITIZE_STRING); $email = filter_var($_POST['email'], FILTER_SANITIZE_EMAIL); // Prepared statement to prevent SQL injection $stmt = $pdo->prepare("INSERT INTO users (name, email) VALUES (?, ?)"); $stmt->execute([$name, $email]); -
Preventing CSRF Attacks
Use anti-CSRF tokens to protect against Cross-Site Request Forgery attacks.
// Generate and store a CSRF token $csrfToken = bin2hex(random_bytes(32)); $_SESSION['csrf_token'] = $csrfToken; // Include the token in forms <input type="hidden" name="csrf_token" value=""> -
Implementing Security Headers
Set security headers to enhance web security. // Enable content security policy (CSP) header("Content-Security-Policy: default-src 'self'"); // Prevent MIME-type sniffing header("X-Content-Type-Options: nosniff"); -
Securing Cookies
Set secure and HttpOnly flags for cookies to prevent data theft.
// Set secure and HttpOnly flags for cookies setcookie("session_cookie", $value, time() + 3600, "/", "example.com", true, true);
These practices help ensure the security of PHP applications by safeguarding user data and protecting against common web vulnerabilities.
7 API Security
API security is crucial to protect PHP applications that expose or consume APIs. Here are key aspects of API security in PHP applications, along with relevant code examples:
-
Authentication and Authorization for APIs
Implement robust authentication and authorization mechanisms to ensure only authorized users or applications can access your API.
// Example using JWT for API authentication $token = generateJwtToken($user_id); -
Rate Limiting and Throttling
Apply rate limiting and throttling to prevent abuse and ensure fair API usage.
// Example rate limiting with Redis $clientIp = $_SERVER['REMOTE_ADDR']; $apiEndpoint = 'api/resource'; $limit = 100; // Requests per minute $key = "rate_limit:$apiEndpoint:$clientIp"; if ($redis->get($key) >= $limit) { http_response_code(429); // Too Many Requests die('Rate limit exceeded.'); } else { $redis->incr($key); $redis->expire($key, 60); // Reset limit after 1 minute } -
Handling API Tokens
Securely manage API tokens and ensure they are not exposed in client-side code or URLs.
// Example of handling API tokens $apiToken = $_SERVER['HTTP_AUTHORIZATION']; if (!isValidToken($apiToken)) { http_response_code(401); // Unauthorized die('Invalid API token.'); }
By focusing on authentication, authorization, rate limiting, and secure token handling, you can enhance the security of your PHP applications when interacting with APIs.
8 Session Management
Proper session management is crucial for PHP application security, ensuring user sessions are protected from unauthorized access and manipulation.
-
PHP Session Security
PHP session management is essential for maintaining user state between requests. However, it must be done securely to prevent session hijacking and other vulnerabilities.
-
Session Start: Always start sessions with session_start(); at the beginning of PHP scripts that require session data.
-
Session Regeneration: Regenerate session IDs periodically to prevent session fixation attacks.
// Regenerate session ID session_regenerate_id(true); -
Session Timeout: Set a reasonable session timeout to invalidate sessions after a period of inactivity.
// Set session timeout (e.g., 30 minutes) ini_set('session.gc_maxlifetime', 1800); -
Secure Cookies: Ensure session cookies are secure and HttpOnly to prevent data theft.
// Set secure and HttpOnly flags for session cookies session_set_cookie_params(['secure' => true, 'httponly' => true]);
-
-
Best Practices for Session Handling
Follow thee best practices for managing sessions in PHP applications to enhance security:
-
Use Strong Session IDs: Generate session IDs with sufficient entropy using session_id().
-
Validate Session Data: Sanitize and validate session data before using it to prevent injection attacks.
-
Destroy Sessions: Always destroy sessions when users log out or no longer need them.
// Destroy session session_destroy(); -
Implement Logout Functionality: Provide a logout feature to invalidate sessions.
-
Avoid Session Fixation: Change session IDs upon login to prevent session fixation attacks.
-
Monitor Session Activity: Keep logs and monitor session activity for suspicious behavior.
-
Proper session management is crucial for PHP application security, protecting user sessions from unauthorized access and manipulation.
9 Third-party Libraries and Dependencies
-
Security Considerations for Third-party Packages
When using third-party packages or libraries in PHP applications, it’s essential to consider security aspects:
-
Dependency Updates: Keep third-party dependencies up-to-date to patch known vulnerabilities. Utilize Composer or package manager commands for updates.
composer update -
Vulnerability Scanning: Use tools like OWASP Dependency-Check or Snyk to scan for known vulnerabilities in your project’s dependencies.
# Example using OWASP Dependency-Check ./dependency-check.sh --project "MyApp" --scan . -
Secure Configuration: Configure third-party libraries securely by following their documentation and security best practices.
-
Code Review: Perform code reviews to identify potential security issues within third-party code.
-
-
Dependency Scanning and Monitoring
Continuous monitoring of dependencies is crucial for PHP application security:
-
Automated Scanning: Integrate automated dependency scanning into your CI/CD pipeline to catch vulnerabilities early.
-
Dependency Monitoring Tools: Use services like GitHub Dependabot or WhiteSource to receive alerts about vulnerabilities in your dependencies.
# Example GitHub Dependabot configuration version: 2 updates: - package-ecosystem: "composer" directory: "/" schedule: interval: "daily" -
Version Pinning: Pin dependencies to specific versions to prevent unexpected updates.
{ "require": { "vendor/package": "1.2.3" } } -
Response Plan: Have a response plan in place for addressing and mitigating vulnerabilities promptly.
-
By considering these security practices for third-party packages and dependencies, you can reduce the risk of vulnerabilities and enhance the security of your PHP applications.
10 Security Testing and Auditing
-
Code Audits
Code audits involve manually inspecting PHP code to identify security vulnerabilities and adherence to best practices.
- Static Analysis: Review the codebase for vulnerabilities like SQL injection, XSS, and CSRF.
- Coding Standards: Ensure that PHP code follows coding standards and best practices, which can prevent security issues.
- Identify Weaknesses: Detect coding patterns that may lead to vulnerabilities and recommend improvements.
-
Penetration Testing
Penetration testing, or ethical hacking, involves simulating attacks on PHP applications to find security weaknesses.
- Manual Testing: Ethical hackers use techniques to exploit vulnerabilities, such as SQL injection, to assess real-world risks.
- Reporting: Detailed reports are generated to highlight vulnerabilities and suggest mitigation strategies.
- Regular Testing: Perform penetration tests regularly, especially after significant code changes.
-
Automated Security Testing Tools
Automated tools help identify common security issues in PHP applications efficiently.
- Static Analysis Tools: Tools like PHPStan and Psalm analyze code for issues like type errors and security vulnerabilities.
- Dynamic Analysis Tools: Tools like OWASP ZAP and Burp Suite scan web applications for vulnerabilities in runtime.
- Dependency Scanners: Tools like Composer’s ‘show’ command and OWASP Dependency-Check identify vulnerabilities in third-party packages.
# Example using Composer to show vulnerabilities composer show --all | grep -i vulnerable - Regular Scans: Automate security scans as part of your CI/CD pipeline for continuous monitoring.
PHP applications benefit from a combination of code audits, penetration testing, and automated security testing to identify and mitigate vulnerabilities effectively. Regular testing and audits are crucial for maintaining a robust security posture.
11 Incident Response and Recovery
-
Developing an Incident Response Plan
Create a detailed incident response plan tailored to your PHP application.
- Identification: Define criteria for identifying security incidents, such as unusual traffic patterns or system anomalies.
- Response Team: Designate a response team with clear roles and responsibilities, including incident coordinators, technical experts, and legal advisors.
- Communication: Establish communication protocols for notifying stakeholders, including customers and regulatory authorities.
- Containment: Develop procedures to contain security incidents and prevent further damage or data loss.
- Eradication: Define steps to eliminate the root cause of security incidents, such as patching vulnerabilities or removing malicious code.
- Recovery: Plan for system recovery, including data restoration and service resumption.
- Lessons Learned: Conduct post-incident reviews to identify improvements in incident response processes.
-
Handling Security Breaches and Data Leaks
In case of a security breach or data leak in your PHP application, follow these steps:
- Isolate the Affected Area: Identify the compromised systems or components and isolate them from the network to prevent further damage.
- Preserve Evidence: Preserve evidence related to the breach, including logs, server snapshots, and any other relevant data.
- Notification: Comply with legal and regulatory requirements by notifying affected individuals, customers, and authorities as necessary.
- Mitigation: Take immediate steps to mitigate the impact, such as closing vulnerabilities and implementing additional security measures.
- Recovery: Work on restoring affected services, systems, or data from backups while fully addressing the breach.
- Legal Compliance: Cooperate with legal authorities and law enforcement agencies in case of criminal activities.
- Documentation: Document all actions taken during the incident response process for future reference and analysis.
Handling security breaches and data leaks in a PHP application requires a well-prepared incident response plan and swift, coordinated action to minimize the damage and protect sensitive information.
12 Security Best Practices for DevOps
The security best practices include the following:
-
Continuous Security Integration (CSI)
Implement Continuous Security Integration (CSI) practices into your DevOps pipeline for PHP applications.
-
Static Analysis: Use static code analysis tools like PHPStan or Psalm to scan PHP code for vulnerabilities during development.
# Example using PHPStan phpstan analyse src -
Dependency Scanning: Utilize automated dependency scanning tools like OWASP Dependency-Check to identify and address vulnerabilities in third-party packages.
# Example using OWASP Dependency-Check dependency-check --project "PHPApp" --scan . -
Security Testing: Integrate security testing into your CI/CD pipeline using tools like OWASP ZAP or Burp Suite to perform dynamic analysis and penetration testing.
# Example using OWASP ZAP zap-baseline.py -t https://phpapp.example.com
-
Static Analysis: Use static code analysis tools like PHPStan or Psalm to scan PHP code for vulnerabilities during development.
-
Container Security
When using containers for PHP applications, consider container security best practices:
- Base Images: Start with a minimal and secure base image to build your PHP application container.
- Image Scanning: Use container image scanning tools like Trivy or Clair to check for vulnerabilities in container images.
# Example using Trivy trivy image php-app:latest - Runtime Protections: Implement runtime protections like AppArmor or SELinux to restrict container processes’ capabilities.
- Network Policies: Define network policies to control network traffic between containers and other services.
-
Server Hardening
Secure your PHP application’s hosting server with these server-hardening best practices:
- Operating System Updates: Regularly apply security patches and updates to the server’s operating system.
# Example for Debian/Ubuntu apt update apt upgrade - Firewalls: Configure firewalls (e.g., iptables, firewalld) to restrict incoming and outgoing network traffic.
# Example using iptables iptables -A INPUT -p tcp --dport 80 -j ACCEPT - SSH Security: Secure SSH access by turning off root login, using SSH keys, and enforcing strong passwords.
# Example: Disable root login in SSH PermitRootLogin no - File System Permissions: Apply the principle of least privilege to file system permissions, restricting access to sensitive directories and files.
# Example: Set directory permissions chmod 700 /var/www/private
- Operating System Updates: Regularly apply security patches and updates to the server’s operating system.
Implementing these security best practices in your DevOps processes for PHP applications ensures that security is an integral part of your development lifecycle, protecting your application and its environment effectively.
Read More: Simplifying Cloud Web Development with Serverless PHP
Bottom Line
Securing PHP applications is a multifaceted process that demands a comprehensive understanding of potential vulnerabilities and implementing proactive measures. By following the step-by-step approach outlined in this guide, you can enhance the security posture of your PHP applications. With the ever-evolving threat landscape, prioritizing security is not optional; it’s a fundamental necessity.
For those looking to fortify their PHP development team or seeking expert assistance in building secure PHP applications, Capital Numbers is here to help. With a team of skilled PHP developers and a proven track record of delivering secure and scalable solutions, we can be your trusted partner in the ever-evolving realm of PHP application security. Ready to discuss your project? Contact us today!















